The Turnout rang in 2019 with a slick new website—a wonderful interface, modern aesthetic, and a great stock photo of design in action. But is it secure?
The Turnout has a wonderful new website—and it’s pretty slick. A wonderful interface, modern aesthetic, and a great stock photo of design in action.
But is it secure?
That’s a hard question since there’s no universally agreed upon baseline security for a website. It’s such a difficult and complicated topic that what’s out there are various standards, best practices, and guidelines for different parts of security. Application security? Check out OWASP. Platform configuration and hardening? There’s two main choices: the Defense Information Security Agency (DISA) STIGs or the Center for Internet Security (CIS) Benchmarks. Or perhaps you need to secure people, process, and technology, and need a more beefy set of standards? Look to the NIST Cybersecurity Framework, ISO 27000, or the CIS Controls. This post is the first in a series that tries to find the signal in the noise or "how to audit the security of a new website." We won’t get to everything, but we can make sure that we hit the high points.
Before we get further, there’s a simple but important question to answer first: Why not just use services like Wix or SquareSpace? These platforms offer high quality design templates, and manage security for their customers. Well, the President of The Turnout is a longtime software engineer. I’m sure he wanted to flex those metacarpals a bit and control his own destiny. Although it takes a little bit of time up front, developing a site yourself is actually much cheaper in the long run. All you really pay for is hosting. Yet as a security professional, this troubles me somewhat—these platforms are automating security and taking my job!
As mentioned before, approaches differ, but my first step in reviewing a website is to inspect the servers and other equipment actually hosting the site. Is The Turnout actually hosting its own server in a closet under the stairs next to Harry? Probably not.

There’s many ways of investigating a server, but I just simply open up a command prompt and use the nslookup tool. This tool looks up a name server and shows the Internet Protocol (IP) addresses hiding behind URLs. Simply open a command prompt or terminal and type: nslookup turnout.rocks
computer:Desktop jtag$ nslookup turnout.rocks
Server: 192.168.1.1
Address: 192.168.1.1#53
Non-authoritative answer:
Name: turnout.rocks
Address: 64.90.36.2
And there you have it, turnout.rocks is located at 64.90.36.2. That’s a Class A address with a subnet mask of 255.0.0.0. Nothing out of the ordinary, which is great. Now IP addresses are generally not secrets—no matter how many hacker movies tell you otherwise. They are the signposts that make the Internet work. With directions in hand, we can then take that IP address (64.90.36.2) and plug it into online tools like Shodan and Censys. These are different types of search engines. They don’t search for websites, instead they search the devices that run the Internet. These search engines have a map of the subway system. All the shops and stores you find once you leave the subway tunnels is the Internet we know and love. Google searches the shops above, Shodan searches the subway below. Almost like a series of tubes.
Dr. Alex Halderman of elections fame is actually the Chief Scientist over at Censys. No real correlation, but I do prefer Censys. After inputting the IP address of www.turnout.rocks into Censys, it shows that the website is hosted on Dreamhost. Their infrastructure shows a hostname of apache2-cabo.barton.dreamhost.com. That’s another piece of useful information to scribble in our notebook. Looking at the geolocation information, it seems like the server is physically located in Los Angeles, California.
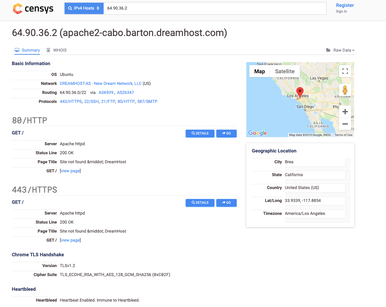
There’s approximately 2000 pounds of useful information here. It’s interesting to see the operating system (OS) listed as Ubuntu. We’ll note that we want to find the exact version number in the near future using a different tool. We also see active ports and protocols supported by the server, like FTP, SSH, SMTP, HTTP, and HTTPS.
Another item on the docket is to snoop a little further into the HTTPS settings supported by the server. This can be an early indicator of whether or not an organization is taking security seriously, since HTTPS (sometimes improperly referred to as SSL) is a fundamental component of web security. A quick check to the URL bar in my browser shows that www.turnout.rocks is actually using HTTPS, which is great, but let’s dip our toes in deeper. One way would be to use a whole bunch of crazy tools and scripts to check out what I’m interested in...or I’ll just try the free service provided by Qualys SSL Labs.
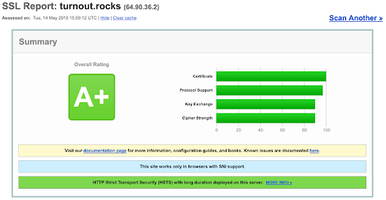
Using Qualys we see that the site has a rating of A+. With an A+ rating, they’re generally doing most everything right. There’s a trusted digital certificate in place. Modern and strong cryptographic ciphers are supported. These protections don’t just protect The Turnout, they also extend to everyone who’s visiting the site. Finally, it’s nice that if you request the unencrypted page with HTTP, the server automatically redirects to the encrypted HTTPS page. That redirection can be difficult to accomplish on some hosting providers.
Another fairly basic check is to visit neighboring websites of The Turnout. Obviously variations of “the” and “turnout” should be considered. The company is formerly named "The Turnout," so at the very least theturnout (dot) rocks should be checked. Looks like turnout (dot) rocks is purchased as is theturnout (dot) rocks. This would be a fairly easy mistake to make for someone who’s new to the organization’s brand, especially if they are looking at The Turnout’s logo which specifically uses the word "The" before "Turnout." Thankfully, all is well. Theturnout (dot) rocks redirects to the main website.
And that’s it for our first post in the series. There’s so much more to explore and we’ll be looking to understand The Turnout’s email setup, usage of HSTS, and if a content management system (CMS) is properly secured. We’ll also explore if there are there any vulnerabilities in the software. You’re just going to have to tune in next time. Don’t worry about the channel though, the entire Internet is a Tivo.

 Joshua M Franklin
Joshua M Franklin

